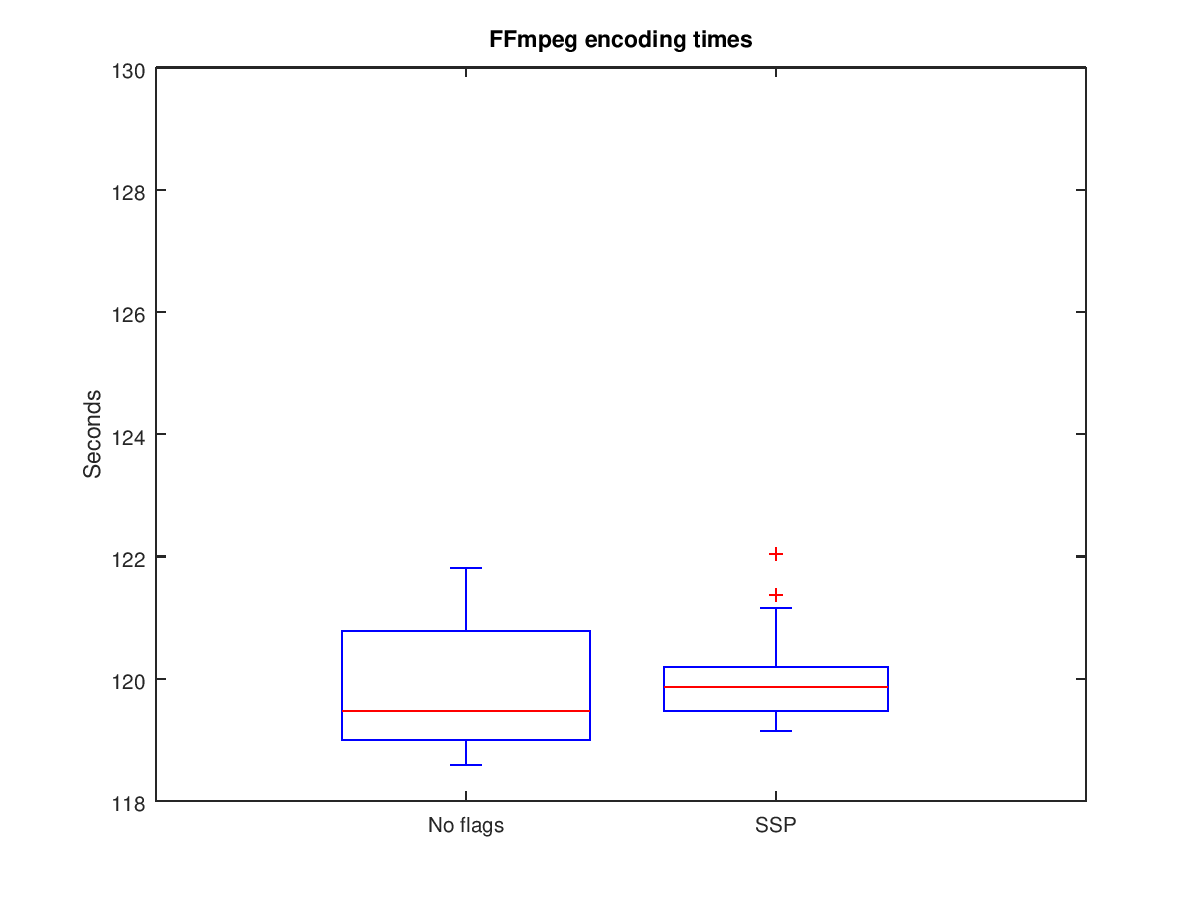
All versions of the toolchain make use of -fstack-protector-all which, although not preventing the issue, will make it harder for an attacker to take control of the execution flow of the program as depending on how the attack is performed the attacker may need to find out the value of the canary in the stack. Buffer overflow protection is any of various techniques used during software development to enhance the security of executable programs by detecting buffer overflows on stack -allocated variables, and preventing them from causing program misbehavior or from becoming serious security vulnerabilities.
Executive summary
With Gentoo Hardened no ebuilds compiled with a hardened toolchain with sys-devel/gcc version 4.8 or higher should be affected by this issue as -fstack-check=specific is enabled by default. The only known exceptions are media-video/vlc and (on HPPA) dev-lang/tcl which disable this feature.
Introduction
The Gentoo Hardened team has been made aware of a set of vulnerabilities known as Stack Clash.
Torrent microsoft office language pack 2007. The language of the Microsoft Office 2007 suite Slovenia. Office 2010 Language Pack add-in products that allow different languages and events. Free Microsoft Office multi-language software package download UpdateStar. Microsoft Office 2007 Language Pack Address multilingual needs. Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian, Japanese) DVD: x64: Italian: Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian, Japanese) DVD: x64: Japanese: Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian.
These vulnerabilities involve the process stack pointer jumping onto other memory regions allowing the attacker to either modify the contents of the stack itself or the memory region on which the stack overflows. As a result, an attacker may be able to modify the data of affected programs or their execution flow and trigger the execution of arbitrary code.
Komik tintin bahasa indonesia lengkap bahasa. The existence of such issues has been known since at least 2005 when Gael Delalleau presented an example of such an issue affecting mod_php in apache.
Requirements to perform the attack
- The attacker needs to be able to move the stack pointer onto an adjacent memory region.
- The attacker needs to ensure this happens without accessing the gap between the stack and the next region.
- The attacker needs to be able overwrite the area where the stack overlaps with the other section in a meaningful way. For example, overwriting the return address of a function to take control of the execution flow.
Effect of Gentoo Hardened protections

As a way to make exploitation of such issues harder vanilla Linux kernels introduced a 4kiB gap between the stack and the other regionscalled guard page, on PaX based kernels like sys-kernel/hardened-sources the size of this gap defaults at 64kiB and can be modified using /proc/sys/vm/heap_stack_gap. As shown by Qualys' advisory, such gap isn't large enough for all allocations and can be jumped over in some cases.
It should be taken into account that this measure was never meant as a final solution as this problem can only be addressed correctly during code generation. Therefore, increasing the size of this gap will not deter all exploitation attempts as large enough allocations may still be able to jump over the gap. It will though affect the processes running on the system and limit the amount of virtual memory space available to them. Although this might not be a problem on 64 bit architectures where the virtual memory space is quite large, on 32 bit architectures this may still be problematic and should be taken into account before using a large heap_stack_gap value.
The Gentoo Hardened toolchain also makes use of sys-devel/gcc's Stack Checking feature using -fstack-check=specific since sys-devel/gcc 4.8. This makes gcc add stack probing code when large allocations are made ensuring that the guard page or the stack gap are accessed. This will then prevent the attack by killing the process.
Although -fstack-check=specific has some known bugs these doesn't seem to affect the specific packages pointed out by Qualys although they might allow exploitability of other yet unknown bugs. Also, since -fstack-check=specific may leave a small (less than 6) number of pages unchecked, use of sys-kernel/hardened-sources is strongly recommended since it has a default gap size of 16 pages in x86 an amd64 arches.
To be fully effective, -fstack-check=specific requires that all the source files used by the process have been compiled making use of this feature. This is because gcc may optimize away some of the checks that are considered redundant.
An assesment over the Gentoo Portage tree hints that only two packages disable this feature. Some ebuilds for media-video/vlc disable the flag to address bug #499996. On the other hand, some ebuilds for dev-lang/tcl disables this feature on HPPA builds to address bug #280934.
It is possible to check the version of the compiler used on a specific ELF binary by checking the value of the .comment section as long as it was not stripped. For this the command readelf -p .comment can be used, for example to check /usr/bin/whoami run the following command:
Users of the split-debug portage feature should instead check the debug file on /usr/lib/debug/. For example the prior example for /usr/bin/whoami would be:
user $readelf -p .comment /usr/lib/debug/usr/bin/whoami.debugAll versions of the toolchain make use of -fstack-protector-all which, although not preventing the issue, will make it harder for an attacker to take control of the execution flow of the program as depending on how the attack is performed the attacker may need to find out the value of the canary in the stack.
In this case caution is advised because the amount of ebuilds disabling SSP is much larger and, shall the frame of any function provided by the binaries generated using these ebuilds end up on the overflowed into memory section, the attacker will be able to overwritetheir return pointer.
All of the binaries in Gentoo Hardened are also compiled as PIE binaries unless ebuilds or the upstream buildsystem disables it. This allows using ASLR which both vanilla and PaX kernels provide with the second being noticeably stronger. This will make it harder for an attacker to figure out a valid address on which to return.
Finally, sys-kernel/hardened-sources allows enabling Deter exploit bruteforcing. This feature limits the number of attack attempts per second that can be made against SUID binaries making exploitation noticeably harder.
On sys-kernel/hardened-sources the increased entropy provided by ASLR will require a large number of attack attempts before succeeding at taking control of the program reliably. This, along with the slowdown introduced by Deter exploit bruteforcing, will make the attack require a huge amount of time to succeed. Because of this, such attacks will be unfeasible in the majority of situations.

Conclusion
With the exception of exploits able to make use of media-video/vlc to jump over the thread gap or (on HPPA systems) dev-lang/tcl users of Gentoo Hardened who have recompiled their userspaces using sys-devel/gcc 4.8 or higher are protected against stack overflow issues.
Users of prior versions of sys-devel/gcc have also partial protection against some of the exploits thanks to ASLR, PIE, Deter exploit bruteforcing and even SSP although they should reconsider rebuilding their userspace with a more modern version of the hardened toolchain.
Further reading reading and sources
Use Stack Protector All (stack Canaries For Mac Os
- bug #CVE-2017-1000377
- bug #499996
- bug #280934
Thanks
The Gentoo Hardened team would like to thank the PaX Team for its outstanding work and its support whilst writting this statement.
We'd also like to thank Zorry for his hard work introducing -fstack-check=specific on the toolchain.
The latest version of this statement can be found on [1]
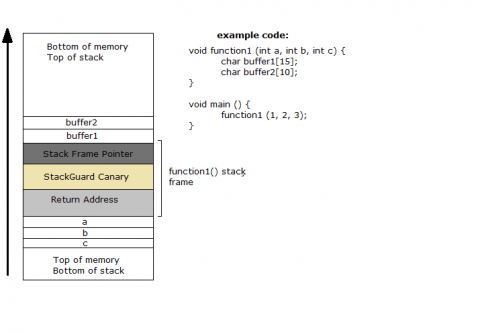
The stack smashing protector is a feature implemented in gcc. When entering function, it stores the return address and frame pointer on stack. And then, it stores a specific guard value called 'canary' on stack. when exit function, it checkes whether this canary value has been changed or not. If the value has been changed, it means buffer overflow is occurred. In this case, it calls 'stack_chk_fail()' function which print error message and exit the program.
Introduction
The Gentoo Hardened team has been made aware of a set of vulnerabilities known as Stack Clash.
Torrent microsoft office language pack 2007. The language of the Microsoft Office 2007 suite Slovenia. Office 2010 Language Pack add-in products that allow different languages and events. Free Microsoft Office multi-language software package download UpdateStar. Microsoft Office 2007 Language Pack Address multilingual needs. Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian, Japanese) DVD: x64: Italian: Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian, Japanese) DVD: x64: Japanese: Disc 1: Office 2007 Multi-Language Pack (x86 and x64) - DVD (English, French, German, Italian.
These vulnerabilities involve the process stack pointer jumping onto other memory regions allowing the attacker to either modify the contents of the stack itself or the memory region on which the stack overflows. As a result, an attacker may be able to modify the data of affected programs or their execution flow and trigger the execution of arbitrary code.
Komik tintin bahasa indonesia lengkap bahasa. The existence of such issues has been known since at least 2005 when Gael Delalleau presented an example of such an issue affecting mod_php in apache.
Requirements to perform the attack
- The attacker needs to be able to move the stack pointer onto an adjacent memory region.
- The attacker needs to ensure this happens without accessing the gap between the stack and the next region.
- The attacker needs to be able overwrite the area where the stack overlaps with the other section in a meaningful way. For example, overwriting the return address of a function to take control of the execution flow.
Effect of Gentoo Hardened protections
As a way to make exploitation of such issues harder vanilla Linux kernels introduced a 4kiB gap between the stack and the other regionscalled guard page, on PaX based kernels like sys-kernel/hardened-sources the size of this gap defaults at 64kiB and can be modified using /proc/sys/vm/heap_stack_gap. As shown by Qualys' advisory, such gap isn't large enough for all allocations and can be jumped over in some cases.
It should be taken into account that this measure was never meant as a final solution as this problem can only be addressed correctly during code generation. Therefore, increasing the size of this gap will not deter all exploitation attempts as large enough allocations may still be able to jump over the gap. It will though affect the processes running on the system and limit the amount of virtual memory space available to them. Although this might not be a problem on 64 bit architectures where the virtual memory space is quite large, on 32 bit architectures this may still be problematic and should be taken into account before using a large heap_stack_gap value.
The Gentoo Hardened toolchain also makes use of sys-devel/gcc's Stack Checking feature using -fstack-check=specific since sys-devel/gcc 4.8. This makes gcc add stack probing code when large allocations are made ensuring that the guard page or the stack gap are accessed. This will then prevent the attack by killing the process.
Although -fstack-check=specific has some known bugs these doesn't seem to affect the specific packages pointed out by Qualys although they might allow exploitability of other yet unknown bugs. Also, since -fstack-check=specific may leave a small (less than 6) number of pages unchecked, use of sys-kernel/hardened-sources is strongly recommended since it has a default gap size of 16 pages in x86 an amd64 arches.
To be fully effective, -fstack-check=specific requires that all the source files used by the process have been compiled making use of this feature. This is because gcc may optimize away some of the checks that are considered redundant.
An assesment over the Gentoo Portage tree hints that only two packages disable this feature. Some ebuilds for media-video/vlc disable the flag to address bug #499996. On the other hand, some ebuilds for dev-lang/tcl disables this feature on HPPA builds to address bug #280934.
It is possible to check the version of the compiler used on a specific ELF binary by checking the value of the .comment section as long as it was not stripped. For this the command readelf -p .comment can be used, for example to check /usr/bin/whoami run the following command:
Users of the split-debug portage feature should instead check the debug file on /usr/lib/debug/. For example the prior example for /usr/bin/whoami would be:
user $readelf -p .comment /usr/lib/debug/usr/bin/whoami.debugAll versions of the toolchain make use of -fstack-protector-all which, although not preventing the issue, will make it harder for an attacker to take control of the execution flow of the program as depending on how the attack is performed the attacker may need to find out the value of the canary in the stack.
In this case caution is advised because the amount of ebuilds disabling SSP is much larger and, shall the frame of any function provided by the binaries generated using these ebuilds end up on the overflowed into memory section, the attacker will be able to overwritetheir return pointer.
All of the binaries in Gentoo Hardened are also compiled as PIE binaries unless ebuilds or the upstream buildsystem disables it. This allows using ASLR which both vanilla and PaX kernels provide with the second being noticeably stronger. This will make it harder for an attacker to figure out a valid address on which to return.
Finally, sys-kernel/hardened-sources allows enabling Deter exploit bruteforcing. This feature limits the number of attack attempts per second that can be made against SUID binaries making exploitation noticeably harder.
On sys-kernel/hardened-sources the increased entropy provided by ASLR will require a large number of attack attempts before succeeding at taking control of the program reliably. This, along with the slowdown introduced by Deter exploit bruteforcing, will make the attack require a huge amount of time to succeed. Because of this, such attacks will be unfeasible in the majority of situations.
Conclusion
With the exception of exploits able to make use of media-video/vlc to jump over the thread gap or (on HPPA systems) dev-lang/tcl users of Gentoo Hardened who have recompiled their userspaces using sys-devel/gcc 4.8 or higher are protected against stack overflow issues.
Users of prior versions of sys-devel/gcc have also partial protection against some of the exploits thanks to ASLR, PIE, Deter exploit bruteforcing and even SSP although they should reconsider rebuilding their userspace with a more modern version of the hardened toolchain.
Further reading reading and sources
Use Stack Protector All (stack Canaries For Mac Os
- bug #CVE-2017-1000377
- bug #499996
- bug #280934
Thanks
The Gentoo Hardened team would like to thank the PaX Team for its outstanding work and its support whilst writting this statement.
We'd also like to thank Zorry for his hard work introducing -fstack-check=specific on the toolchain.
The latest version of this statement can be found on [1]
The stack smashing protector is a feature implemented in gcc. When entering function, it stores the return address and frame pointer on stack. And then, it stores a specific guard value called 'canary' on stack. when exit function, it checkes whether this canary value has been changed or not. If the value has been changed, it means buffer overflow is occurred. In this case, it calls 'stack_chk_fail()' function which print error message and exit the program.
There are gcc options which enable/disable stack smashing protector.
-fno-stack-protector : disables stack protection. This is default option.
-fstack-protector : enables stack protection for vulnerable functions that contain buffers larger than 8 bytes. This includes functions that call 'alloca'.
-fstack-protector-all adds stack protection to all functions.
-fstack-protector-strong : like -fstack-protector. but it includes additional functions that have local array definitions, or have references to local frame address.
In this post, let's see about -fstack-protector-all.
source code
In this code, the element count of buf array is 2.
compile(generate executable file)
enables -fstack-protector-all.
compile(generate assembly code)
generates assembly code to see how stack smashing protector works.
output(with enabling -fstack-protector-all)
Warhammer 40 000: dawn of war ii: retribution download for mac iso. Here, input 3 or larger value to make buffer overflow.
Error message is printed and the program is exited.
generated assembly code
Let's see 'testFunc1' label
Use Stack Protector All (stack Canaries For Macs
Here is a snippet of testFunc1 and relevant code. I added @comment here.
Use Stack Protector All (stack Canaries For Macular Degeneration
In gcc source code, __stack_chk_fail() is as below.
